Understanding NTLM: The Predecessor to Kerberos
I originally planned to dive straight into Kerberos vulnerabilities, but then I thought, “Why not start at the beginning?” Before we can understand the issues with Kerberos, it’s important to know what it is and how it works.
Kerberos is a network authentication protocol, and it’s the default method used on Windows today.
But before Kerberos, there was something called NTLM.
NTLM
Windows New Technology LAN Manager (NTLM) is a suite of security protocols offered by Microsoft to authenticate users’ identity. It is implemented using challenge-response protocol to confirm the user without requiring them to submit a password.
How NTLM Works
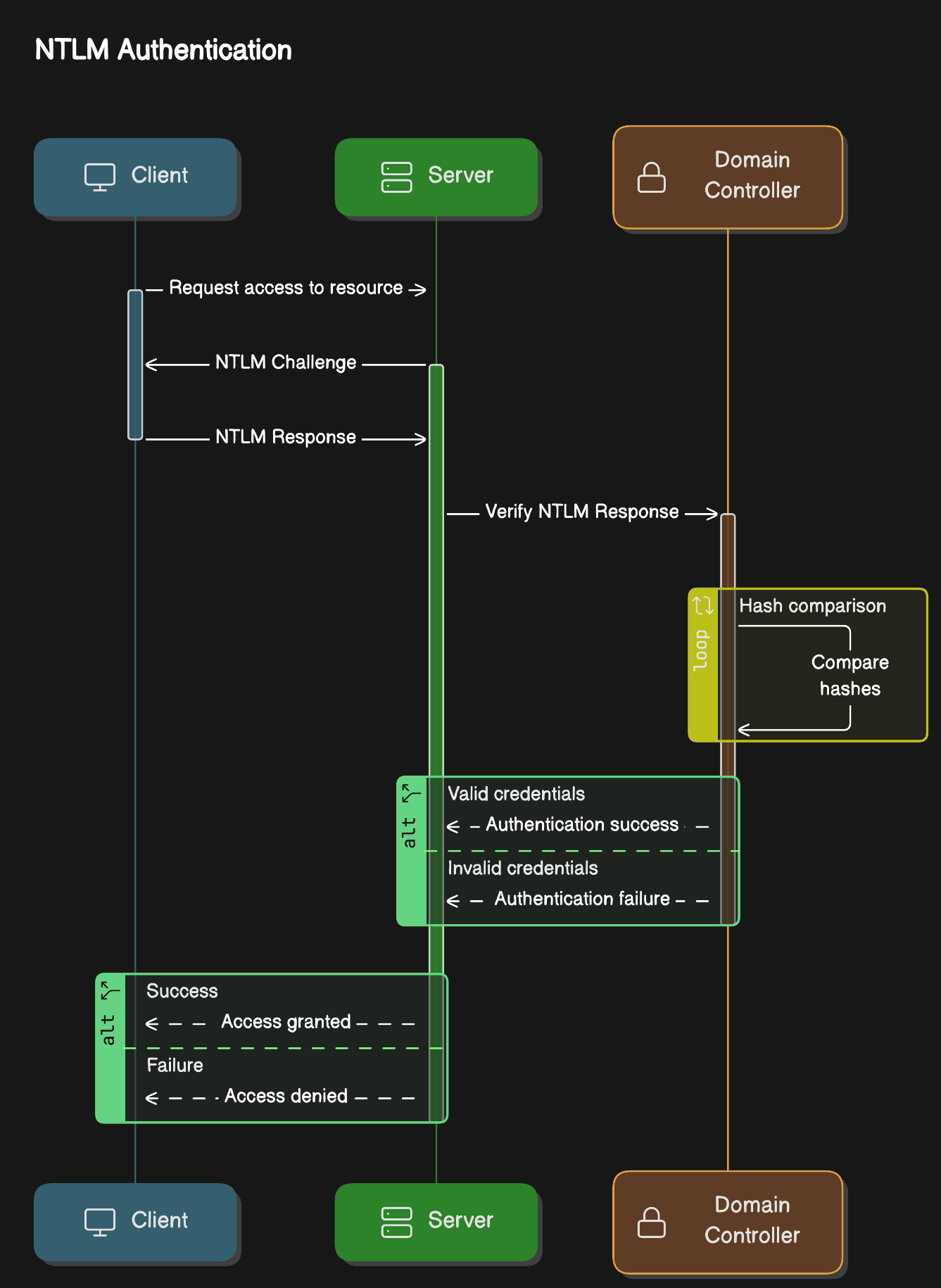
- The client sends an authentication request to the server they want to access.
- The server generates a nonce and sends it as a challenge to the client.
- The client combines their NTLM password hash with the challenge (and other known data) to generate a response to the challenge and sends it back to the server for verification.
- The server forwards the challenge and the response to the Domain Controller for verification.
- The domain controller uses the challenge to recalculate the response and compares it to the original response sent by the client. If they both match, the client is authenticated; otherwise, access is denied. The authentication result is sent back to the server.
- The server forwards the authentication result to the client.
Computing the correct response requires knowledge of the user’s password. So the server can validate the response by consulting an account database such as AD to get the user’s password and computing the proper response for that challenge.
NTLM in Context
NTLM isn’t a standalone protocol, it works within other higher-level application protocols, embedding its messages in their data payloads. These parent protocols handle the network communication, while NTLM handles the authentication part.
If you’re interested in the detailed technical specifications, you can refer to the official documentation here.
Why NTLM Still Matters
Even though Kerberos has largely replaced NTLM, there are still situations where NTLM is used:
- Legacy Systems: Some older systems or applications may not support Kerberos.
- Non-Domain Joined Machines: NTLM is used when machines aren’t part of a domain since Kerberos requires domain membership.
- Misconfigurations: NTLM can serve as a fallback if Kerberos isn’t set up correctly.
- Explicit Usage: Sometimes, NTLM is chosen directly for specific reasons.
Conclusion
NTLM has played an important role in the history of Windows authentication. While Kerberos is now the go-to protocol, NTLM still has its place. In my next post, I’ll try to explain Kerberos and then we are ready for some vulnerabilities.